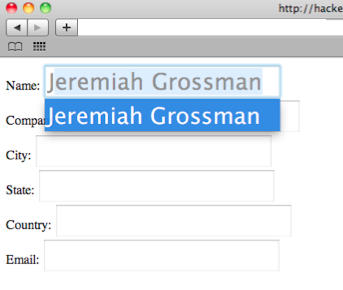
If you use Safari as your main web browser, you might want to open your preferences, switch to Autofill and untick the option to autofill web forms using info from your Address Book card: a serious vulnerability in Safari allows websites to steal information from your Address Book without any user input at all.
The exploit was discovered by Jeremiah Grossman. Here’s how it works:
All a malicious website would have to do to surreptitiously extract Address Book card data from Safari is dynamically create form text fields with the aforementioned names, probably invisibly, and then simulate A-Z keystroke events using JavaScript. When data is populated, that is AutoFill’ed, it can be accessed and sent to the attacker…
As shown in the proof-of-concept code… the entire process takes mere seconds and represents a major breach in online privacy. This attack could be further leveraged in multistage attacks including email spam, (spear) phishing, stalking, and even blackmail if a user is de-anonymized while visiting objectionable online material.
Grossman submitted the exploit to the attention of Apple over a month ago, but decided to publicize it after failing to receive a non-automated response about the matter.
For now, no need to panic, just shut off autofill until Apple works out a fix.
[via Cult of Mac]