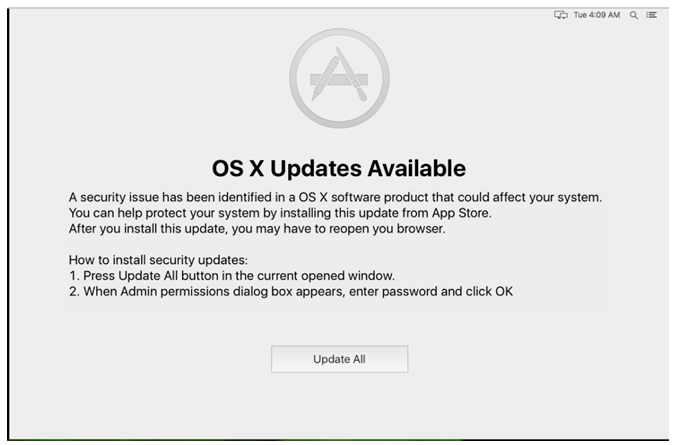
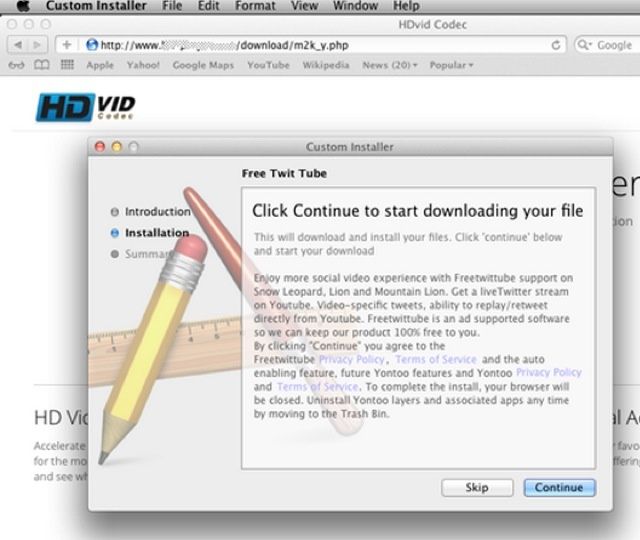
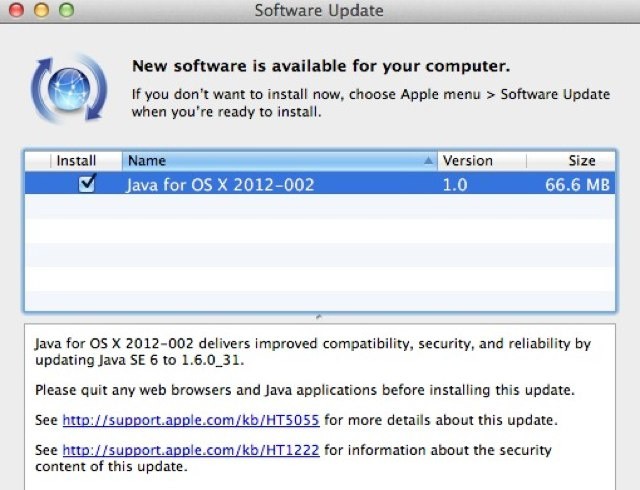
For the first time, an iOS trojan has been spotted in the wild. Adapted from a well-known Android trojan, GoldDigger, the new malware is called GoldPickaxe, according to a new report. And it steals an iPhone user’s facial recognition data to go after money in banking and other financial apps. We’ll show you how below.
First-ever iOS trojan steals your face to break your bank [Updated]
![First-ever iOS trojan steals your face to break your bank [Updated] Trojan horse: first ios trojan goldpickaxe](https://www.cultofmac.com/wp-content/uploads/2024/02/pexels-kemal-hayit-6474435-1536x1022.jpg)
Photo: Pexels-Kamal-Hayit





![Flashback Malware Was Worth Up To $10,000 A Day To Its Creators [Report] The Flashback infection could have generated more in 7 days then most will earn in a year.](https://www.cultofmac.com/wp-content/uploads/2012/05/iStock_money-tree.jpg)





![How To Remove MACDefender Malware Software [Video How-To] m](https://www.cultofmac.com/wp-content/uploads/2011/05/m.png)