1Password has been hovering near the top of the App Store’s charts since it went freemium alongside the launch of iOS 8. Developed by Canadian company AgileBits, the popular password manager has been on the forefront of app development for Apple’s latest OS since WWDC in June.
After releasing an iOS 8-compatible version with iCloud Drive sync, Touch ID integration, and an adaptive layout, 1Password 5.1 is out today with more refinements.
The iPhone 6 and 6 Plus are both fully supported now, which means a non-steched interface.
While Touch ID could be used to authenticate the app before today, a master password was still required after quitting and re-opening. Many tricked 1Password into always authenticating with Touch ID by setting the app’s login settings to 30 days, but version 5.1 makes that no longer necessary. If enabled, you’ll no longer need to type in a password to unlock the app’s vault.
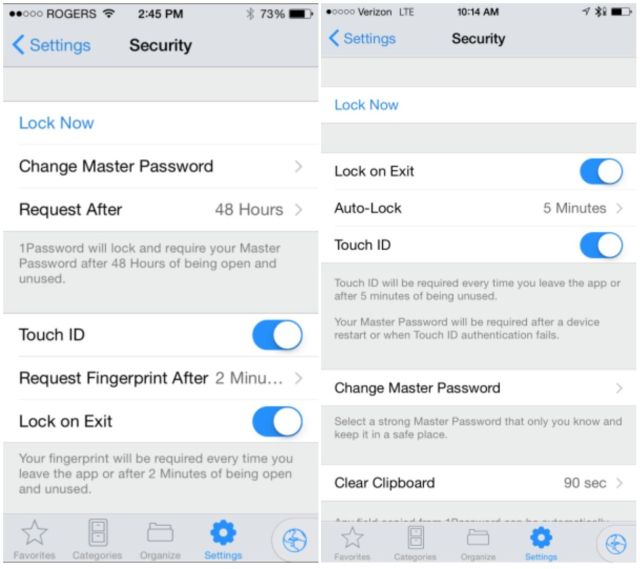
“The Auto-Lock timeout will now function across both the Master Password and Touch ID/PIN Code, removing the confusion the separate settings caused,” reads the update description. “The iOS Keychain will be used to store the Master Password when Touch ID/PIN Code is enabled, allowing Touch ID/PIN Code to be used reliably in the 1Password Extension.”
For more about how 1Password incorporated the Touch ID API, check out the AgileBits blog.
Finally, third-party keyboards can be enabled under settings. The reason for blocking them by default is that many are capable of logging keystrokes, which is something the security-focused developers at AgileBits obviously want to avoid.
Not only can 1Password be accessed nearly anywhere in iOS 8 thanks to its Share sheet extension, but many of the best third-party apps available support 1Password for entering login details. Thanks to the warm embrace of the developer community and the flexibility of iOS 8, 1Password is truly a viable (and in many cases) better alternative to Apple’s iCloud Keychain.
1Password is free to download and try in the App Store, and a $10 in-app purchase unlocks full functionality.


4 responses to “1Password cements itself as a staple iOS 8 app with new update”
I signed into this forum using 1password and touch ID! No typing required…even on this third party keyboard that I’m using.
If only Apple would fix the bug that won’t keep the 1Password button pinned to the front of the Safari share sheet.
I have 1Password on my Win-7, iPad 2 iOS 8, and iPhone 4S iOS 7.n. iPad is now running 1Password 5.1 but my iPhone 4S iOS 7 is at 1Password 4.5.3 and the AppStore does NOT show any updates. Has 1Password stopped supporting the iPhone 4S iOS 7?
ID federations (single-sign-on services and password managers) create a single
point of failure, not unlike putting all the eggs in a basket. It remembers all my passwords when un-hacked and loses all my passwords to criminals when hacked. It should be operated in a decentralized formation or should be considered mainly for low-security accounts, not for high-security business which should desirably be protected by all different strong passwords unique to each account. Needless to
say, the strength of the master-password is crucially important.
Apple is expected do something about the vulnerability that their Touch ID brings:
Biometrics operated with a password in the OR/disjunction way (as in the case of iPhone) offers a lower security than when only the password is used.
Biometrics can theoretically be operated together with passwords in two ways, (1) by
AND/conjunction or (2) by OR/disjunction. I would appreciate to hear if someone knows of a biometric product operated by (1). The users of such products must have been notified that, when falsely rejected by the biometric sensor with the devices finally locked, they would have to see the device reset. It is the same with the biometrics operated without passwords altogether.
Biometric products like Apple’s Touch ID are generally operated by (2) so that users can unlock the devices by passwords when falsely rejected by the biometric sensors. This means that the overall vulnerability of the product is the sum of the vulnerability of biometrics (x) and that of a password (y). The sum (x + y – xy) is necessarily larger than the vulnerability of a password (y), say, the devices with Touch ID and other biometric sensors are less secure than the devices protected only by a password.
It is very worrying to see so many ICT people being indifferent to the difference between AND/conjunction and OR/disjunction when talking about “using two factors together”.