If you’re as confused as we were when we first heard about the major App Store hack over the weekend, we’re here to help.
Here’s a compilation of everything we know about the XcodeGhost story, and we’ll be updating it as more develops.
What is XcodeGhost?
The XcodeGhost hack represents the first widespread malware incident in the iOS ecosystem, and it uses Apple’s own architecture against it.
Xcode is Apple’s programming framework that developers use to create the apps you use and the games you play. And a modified version of this system is responsible for the issues we’ve been seeing today. XcodeGhost uses an older version of Xcode to introduce malicious functionality into apps without the developers even knowing it’s there. Any app made using the compromised version of Xcode is potentially compromised.
The bad Xcode … code got to developers via industry forums, Lookout reports. It was especially enticing to Chinese developers because they could download the Ghost version faster than the official one directly from Apple. They didn’t know it was modified, so when they used it to make their apps and submitted them to the App Store, the Ghost code stowed away inside of it.
What does XcodeGhost do?
XcodeGhost sits in the background of legitimate apps and mines them for data like an invisible person cheating on a test. Once the affected app launches, it starts picking. The stuff it looks for includes the name of the infected app, the app bundle identifier (a code specific to the developer and app set during submission), the device’s name and type, location and language info, network information, and the device’s “identifierForVendor” (a code that helps to connect apps from the same developer running on the same device).

Photo: Charles Rondeau/Public Domain Pictures
Once it has this information, Ghost sends it to an external server, security firm Palo Alto Networks says. As for what it does with this info? Palo Alto says that the malware has the ability to receive commands from the server which could result in forcing your iOS device to open web pages or create fake prompts to trick you into giving up your Apple ID and password. It could even possibly access data in your clipboard to steal passwords you have stored in a management app, Palo Alto says.
Which apps are affected?
Because of Ghost’s distribution through China-based developer forums, most of the infected apps are from that country. We’ve compiled a list of all of the known affected apps, so check there to see if you’re at risk.
What can you do?
You’re going to want to be proactive if you’re carrying one of these apps, so your first move is to delete any of them you currently have installed. You can also check out our guide of handy tips for more suggestions, like being sure you know where dialogue boxes are coming from and changing your Apple password just in case.
Who did this?
We don’t know, but a post on code-sharing site GitHub by someone claiming to be XcodeGhost’s creator offers some possible answers. [Note: We’ve translated this text from Chinese using Google Translate and attempted to clean it up for clarity, so some translation errors may be present.]
First of all, I apologize for the confusion XcodeGhost has brought. XcodeGhost is from my own experiments, without any threatening behavior, as detailed in the source code.
The so-called XcodeGhost is actually hard to for unsuspecting iOS developers to find. A modified Xcode compiler configuration text file code can be loaded, so I wrote the code above to try and upload it to their network disk.
All data in the code actually acquires basic app information: application name, application version number, system version number, language, country name, developer, app installation time, device name, and device type. In addition, it does not gather any other data. I must confess that for selfish reasons, I used the advertising features in the code to promote these applications (you can confirm this in the source code). But in fact, from the beginning to the final shut down the server, I have not used the advertising function. And 10 days ago, I have taken the program off the server and removed all data, but that will not have any effect on anyone.
In order to put an end to the rumors, the so-called “XcodeGhost” was an ill-advised experiment, and it is now dead.
I wish to emphasize that XcodeGhost-infected apps will not affect any users and does not obtain private data, only a useless piece of code.
Again, I sincerely apologize and wish you a pleasant weekend.
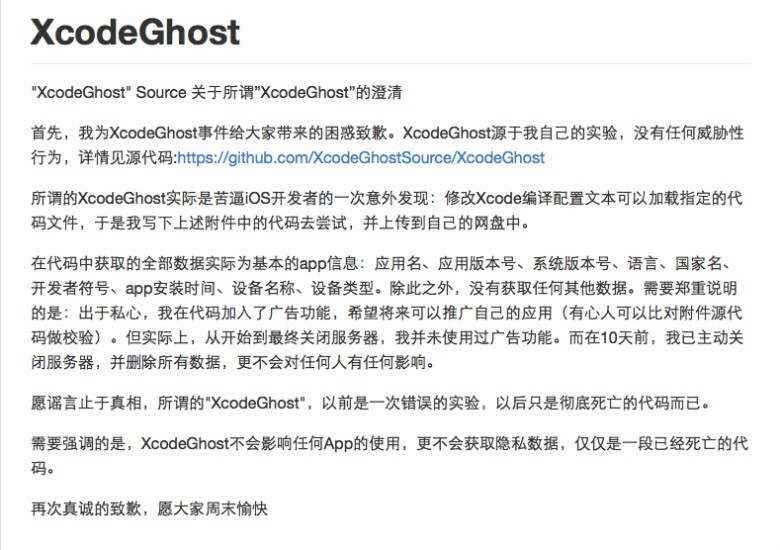
Photo: GitHub
Again, we don’t know that this statement is from the actual creator of the malware, but if it’s true, the hack shouldn’t affect any more apps going forward. We still advocate caution, however.
Does XcodeGhost affect apps in every App Store?

Photo: Rovio Entertainment
The quick answer to this question is that it depends on the app. Isn’t that helpful?
For example, developer Rovio’s game Angry Birds 2 is listed among those affected, but the company claims that only certain versions have the vulnerability.
“Rovio can confirm that the Chinese build of Angry Birds 2, which was available only on the App Store in Mainland China, Taiwan, Hong Kong and Macau, was one of the iOS apps made vulnerable to the security issue,” Rovio said (via AppAdvice). “All other builds of Angry Birds 2 available in all other territories are completely safe and secure.”
So basically, if a developer outsourced the Chinese build of their app to a Chinese developer, then that particular version may have Ghost all up in it. And if the developer made all versions of their app with infected code they got from one of those forums, it will be in all versions. But if they got their Xcode directly from Apple, it’s safe.
We kind of have to go case-by-case on this, and it’s all pretty confusing. But just assume that if an app from the list above is on your device, it could be compromised.



5 responses to “FAQ: Everything you need to know about the XcodeGhost App Store hack”
Technically, XcodeGhost doesn’t do anything “bad”. An App is supposed to collect user data and send back for analyzing, especially for these which use internet services extensively. The only problem is that the creators were unaware of such behavior.
XcodeGhost is not the type of some ultra-genius hack. It’s nothing more than a customized library and modified default project template. Many organizations have similar policies that request employees to use enterprises specified template and libraries for routine works, such as collect user data, in all their products. If XcodeGhost is distributed solely within an organization, and all members are aware of its existence, there is nothing wrong about it at all.
For the similar concept of malicious attacks, XcodeGhost is even considered as “mild”. A more dangerous threat is 3rd party libraries. 3rd party libraries are far easier to modify and distribute. Anyone who compile his Apps with these breached 3rd party libraries, will have malicious code injected automatically. And It is not possible for Apple to whitelist all the 3rd party libraries.
Thanks to Apple’s hysteria on privacy, these “malicious code” still can’t savage your system nor access anything you have not approved.
It can only collect very limited, semi-anonymous information. Now we all know why Apple had intended to add these restrictions.
Allow me to show you~ a fantastic ways to earn a lot of extra money by finishing basic tasks from your house for few short hours a day — See more info by visiting >MY___{DISQUS}___ID::
Allow me to show you a fantastic ways to earn a lot of extra@ CASH by finishing basic tasks from your house for few short hours a day — See more info by visiting >MY_DISQUS_ACCOUNT
“FAQ: Everything you need to know about the XcodeGhost App Store hack”
Thanks for this extended info. Even without the so-called dev’s so-called apology, this whole thing has been blown •way• out of proportion. Listening to US Presidential candidates poses a much greater risk than XcodeGhost.
Can’t say I’m taken by surprise. How many times do things like this have to happen year after year for people to stop buying or using hardware and software from China?
Everyone already knows China is not trustworthy or ethical, but they seem to forget this fact when looking at a cheap price tag.
This latest issue is just one out of many more worse attacks or vulnerabilities executed by the Chinese that don’t even get discovered or publicized.
It’s always been a no brainer that we should avoid all Chinese products.