Apple’s two-step authentication process is designed to make your Apple ID more secure. When attempting to reset a password or make other kinds of account changes, a separate verification code is sent to an iOS device you own. That code is then used to verify that you are who you claim to be before you’re allowed to make any changes.
Many big tech companies have offered two-step authentication for quite some time, and Apple’s process is only a couple months old.
Now that security researchers have had time to dig through Apple’s implementation of two-step, some problems have surfaced. Once the login details for an Apple ID with two-step authentication enabled are compromised, there’s nothing stopping hackers from accessing iCloud data, like device backups.
ElcomSoft, a company that specializes in password cracking software, has published a new report highlighting the secure holes in Apple’s two-step authentication process:
In its current implementation, Apple’s two-factor authentication does not prevent anyone from restoring an iOS backup onto a new (not trusted) device. In addition, and this is much more of an issue, Apple’s implementation does not apply to iCloud backups, allowing anyone and everyone knowing the user’s Apple ID and password to download and access information stored in the iCloud. This is easy to verify; simply log in to your iCloud account, and you’ll have full information to everything stored there without being requested any additional logon information.
In ElcomSoft’s opinion, this is just not the right way to do this from a security point of view. iCloud has been exploited in the past and will be exploited in the future.
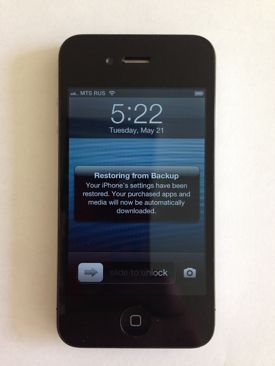
The report goes on to demonstrate how knowing an Apple ID’s login details grants full access to device backups stored in iCloud. ElcomSoft was able to download a backup using the ID’s login details without ever coming into contact with two-step authentication. The physical iOS device that the backup came from wasn’t needed; ElcomSoft simply loaded it onto a new device and restored.
Another security issue is that Apple sends two-step verification codes directly to an iOS device’s lockscreen, which means that anyone could get the PIN without unlocking the device. A hacker would have to have physical access to the device for that to work, however. ElcomSoft suggests that the verification code not be displayed on the lockscreen so that the user would have to enter the device’s unlock passcode first.
“For a record, I’d like to say that Apple’s approach in implementing two-factor authorization does not look like a finished product,” said Vladimir Katalov of ElcomSoft in the report. “It’s just not as secure as one would expect this solution to be.”
It’s important to note that the aforementioned hack would only happen if a victim was being specifically targeted, and you can never have a 100% guarantee that data stored on the internet won’t be compromised.
Apple’s two-step authentication feature is currently available in the United States, UK, Australia, Ireland, New Zealand. Mexico, Germany Netherlands, Russia, Austria, Brazil, Belgium, Portugal, Italy and Poland. Two-step authentication can be enabled under your Apple ID’s “Password and Security” settings on the web.
Source: ElcomSoft
Via: Ars Technica
Image: CNET


