1Password by AgileBits is a an incredible tool for keeping your data safe. More than just a password manager, 1Password allows you to encrypt and organize a wide range of data (website passwords, non-web digital accounts, credit/debit card numbers and financial account details, software licenses, and files containing confidential information.
Those features are all well and good, but the biggest feature is 1Password’s ability to keep all that data secure in the face of brute force attacks – the kind of attacks where a piece of software simply tries combination after combination of possible passwords. Password cracking software that rely on such attacks can easily try thousands of potential passwords each second.
To find out whether or not 1Password can withstand such attacks, AgileBits tested one 1Password against John the Ripper, one of the most well-known password cracking tools.
AgileBits recently detailed much of the investigation and background information on its blog including the fact that John the Ripper and other password cracking tools can be fine-tuned to attack specific encryption tools like 1Password.
The key concept here is that these tools attack the master password that users set when they configure 1Password. Breaking the encryption mechanisms and decrypting data isn’t a viable attack option against high-level encryption technology like that employed by 1Password or Apple’s FileVault. The primary vulnerability in secure systems like 1Password is the credentials that allow the owner (or authorized individuals) of the data to unlock the system. In the case of 1Password that means the master password (in other systems it could be user account and password, two-factor authentication that involves a physical or data token that needs to be presented with a password, or even biometric data like a finger print).
It’s that point of entry that AgileBits tested and studied John the Ripper against. Ultimately, given enough time, John the Ripper will eventually crack any master password. The best that 1Password can do is to build complex calculations into the system – calculations that must be performed with each password attempt. That may not sound like much, but it does work – provided the master password is long enough and random enough.
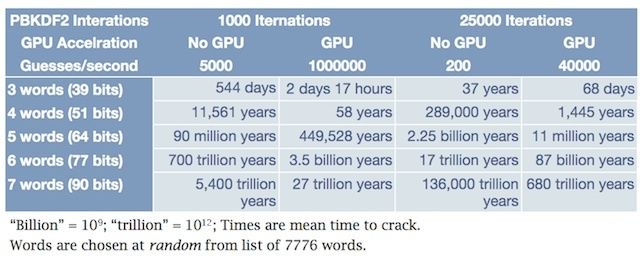
Both of those are important pieces of the solution. The longer the password, the more guesses a cracking tool needs make to get the right password. If you layer on thousands or tens of thousands of complex calculations that need to be performed for each guess, it becomes plausible to stop the attack – or more accurately slow it down the point of effectively stopping by making the cracking tool take days, weeks, years, centuries, or even millennia before every possible combination is tried.
Applying that concept to everyday use, AgileBits suggests that you use multi-word passwords and the words are truly random (rolling dice to select words is one truly random suggesting the company makes). As you can see in the tablet below, a seven word passwords would take trillions of years. Even a four-word password would be sufficient as it would take decades or centuries to crack.