Many of us pass our Macs and some external devices on to others when we upgrade. Family and friends may get our hand-me-downs, but quite frequently we’ll sell an old Mac, printer, or external drive on eBay or some other venue. Regardless of where our computers and related technology end up when we outgrow them, it’s important to make sure we scrub any personal data from them.
The importance of securely erasing personal and/or business data from hardware that is being passed on, sold, or even recycled was highlighted in a recent study by Britain’s Information Commissioner’s Office, which discovered that half of all used hard drives contained information from their previous owners.
The study found that 48% of used drives contained some residual data. 11% contained personal information of some kind. 3% contained sensitive personal details like digital copies of passports and driver’s licenses, birth certificates, tax information, banking and financial information, and health-related data. 1% had enough information on them to commit identity theft.
The study included drives from a mix of sources, including businesses that might be responsible for recording and tracking some of that sensitive data.
Of the drives that didn’t contain accessible data, only 38% we truly clean (meaning that they were securely wiped). The remaining 14% were damaged and considered unreadable though the study doesn’t specify the damage or whether data recovery or forensic tools might have gained information for them.
Those are some troubling statistics, but the big lesson is that if we, as individuals or businesses, are getting rid of drives or computers, we need to securely erase our data.
That means doing more than clicking the simple Erase button in Disk Utility. A simple erase doesn’t actually erase anything. It simply marks all the sectors of a disk as free space. Until every sector has new data stored in it, the old data still exists and data recovery and forensic tools can retrieve it. A secure erase actually overwrites data.
Performing a secure erase is quite simple. Launch Disk Utility, select the drive, and then the Erase tab. On that tab, click the Security Options button and select the type of secure erase you want to perform – there are three choices:
- A single pass erase overwrites the entire drive with a series zeroes. It’s fastest, but data recovery or forensic tools can still recover data.
- A three pass erase writes random data to the drive, then does it again, and then does a standard pass with known data. That’s generally sufficient to prevent most tools from recovering usable data.
- A seven pass erase makes seven passes with specific mixes of known and random data. The process meets U.S. Department of Defense requirements for secure erase of even the most sensitive information. For individuals, this can be overkill, but for businesses that deal with sensitive information like healthcare records or banking/financial data, this is the best option.
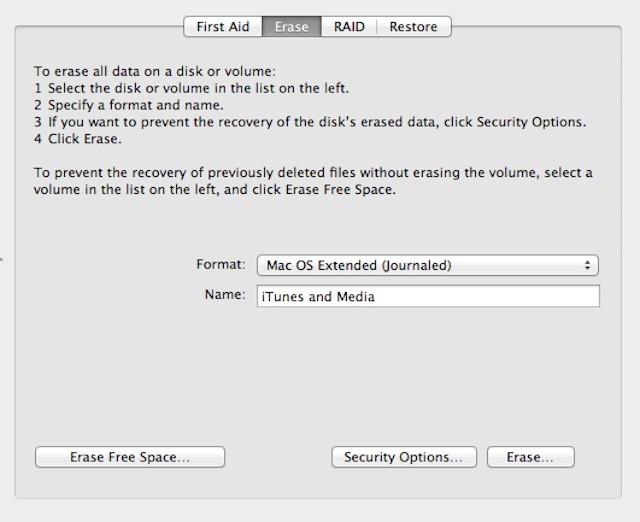
It’s also worth noting that you don’t have to wait until you’re getting rid of a Mac or drive to securely erase information. The Finder’s Secure Empty Trash command performs a single pass erase of data you’re deleting. You can also use Disk Utility’s Erase Free Space option with the same secure erase options available for drives – meaning that any data that you deleted will get overwritten one, three, or seven times but any other data will be left intact.
In addition to Disk Utility, most commercial hard drive tools also offer secure erase features.


