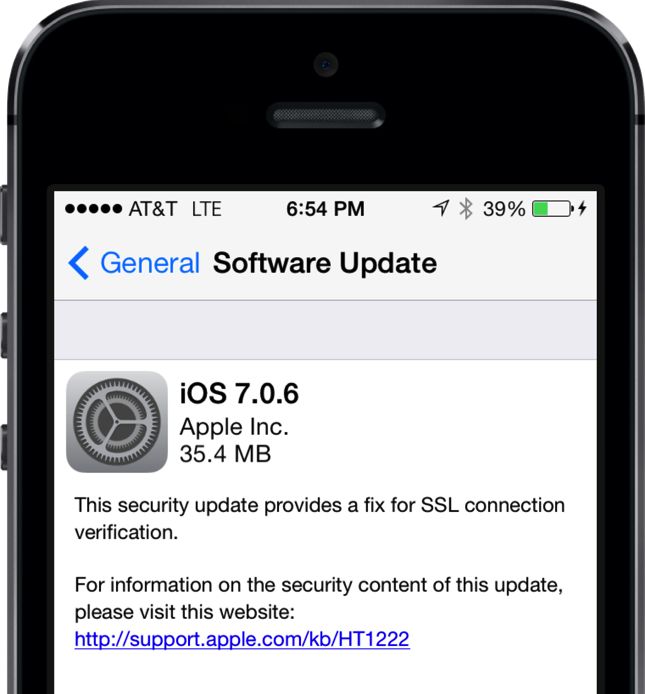
On February 21st, Apple released iOS 7.0.6, a small software update that provided “a fix for SSL connection verification.” The same SSL fix was also released for older iOS 6 devices and the Apple TV. Apple pushes out smaller bug fixes from time to time, so at first glance 7.0.6 seemed like a pretty normal update.
But in reality, Apple patched a major security flaw that has potentially compromised millions of peoples’ data for years. Nicknamed “gotofail,” the bug has been flying under the radar for quite some time, and it still hasn’t been patched in OS X.
Gotofail has allegedly been present since the introduction of iOS 6, and the implications are quite severe. Until now, iOS devices using the internet over a SSL connection have been vulnerable to hackers intercepting their data, or “man-in-the-middle” attacks.
Basically, the bug allows for secure web traffic over SSL/TLS to be hijacked by someone else on the same network. It’s a relatively simple process for anyone with knowledge of the flaw.
The security firm CrowdStrike explains:
Due to a flaw in authentication logic on iOS and OS X platforms, an attacker can bypass SSL/TLS verification routines upon the initial connection handshake. This enables an adversary to masquerade as coming from a trusted remote endpoint, such as your favorite webmail provider and perform full interception of encrypted traffic between you and the destination server, as well as give them a capability to modify the data in flight (such as deliver exploits to take control of your system).
Gotofail is limited to Apple’s apps and services, like Safari and Messages. So third-party browsers like Chrome should be fine.
Many parts of OS X are still vulnerable, including Apple’s software update mechanism.
Here are some of the apps which rely on the vulnerable Apple #gotofail SSL library beyond Safari /cc @a_greenberg pic.twitter.com/ombDOOa01A
— ashkan soltani (@ashk4n) February 23, 2014
Other well-known hackers have expressed concern over the findings:
It takes no iOS expertise for bad guys to abuse the SSL bug Apple just fixed. Many more can exploit (for bad) SSL bug than a normal iOS bug
— MuscleNerd (@MuscleNerd) February 22, 2014
People on public wifi networks (Sochi?), please just don’t use your iOS device if it’s not updated to iOS 7.0.6. Don’t use your Mac Book. — pod2g (@pod2g) February 22, 2014
Yeah, the security of iOS < 7.0.6 is now so bad that I advice everyone to update quick. — pod2g (@pod2g) February 22, 2014
Not difficult to understand: HTTPS doesn’t work on OSX and iOS < 7.0.6. Your passwords and credit card creds can be intercepted on networks.
— pod2g (@pod2g) February 22, 2014
Even banks are contacting their customers and advising them to update to iOS 7.0.6 immediately. “You should install this update as soon as you can to ensure your information is as safe as possible,” warned the online-only bank Simple in an email to customers yesterday.
What is perhaps most alarming about all of this is the theory posited by Daring Fireball’s John Gruber. Gotofail was introduced with the release of iOS 6 in September 2012, and Apple was added to the NSA’s “PRISM” spying program in October 2012.
Once in place, the NSA wouldn’t even have needed to find the bug by manually reading the source code. All they would need are automated tests using spoofed certificates that they run against each new release of every OS. Apple releases iOS, the NSA’s automated spoofed certificate testing finds the vulnerability, and boom, Apple gets “added” to PRISM.
Or, maybe nothing, and this is all a coincidence.
Apple issued a statement last night, per Reuters, saying it was aware of the same SSL bug that still exists in OS X. A fix will be issued soon:
Apple Inc said on Saturday it would issue a software update “very soon” to cut off the ability of spies and hackers to grab email, financial information and other sensitive data from Mac computers.
Confirming researchers’ findings late Friday that a major security flaw in iPhones and iPads also appears in notebook and desktop machines running Mac OS X, Apple spokeswoman Trudy Muller told Reuters: “We are aware of this issue and already have a software fix that will be released very soon.”