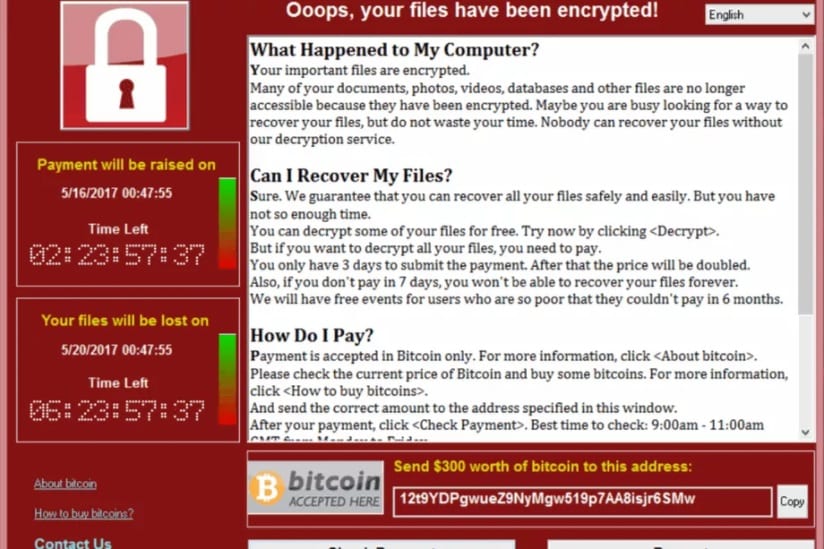
More than 230,000 computers in 150 countries have been hit by a cyberattack that encrypts data until a ransom has been paid. It’s thought to be the biggest in history, with India, Taiwan, and several European countries being the worst effected.
If you use a Mac, you have nothing to worry about for now, since this particular “ransomware” only targets Windows PCs. However, the number of attacks built for macOS is rising at a rapid rate every year.
So, what exactly is ransomware, and how can it be avoided? Here’s what you need to know.
This widespread attack first surfaced in London on Friday morning, with the UK’s National Health Service (NHS) one of the biggest organizations to be hit. It then made its way to more than 150 countries, putting businesses small and large on their backs.
It is believed that the team behind the attack, known as “WannaCrypt” or “WannaCry,” have only received around $32,000 in ransom fees so far, but it is estimated that hundreds of millions of dollars have been lost as a result of computer outages.
Microsoft has described the attack as a “wake-up call,” and it blames governments for “stockpiling vulnerabilities” in software that allowed the ransomware to be created.
Here’s what we know about it so far.
What is ransomware?
Ransomware is a type of malicious software that encrypts the data on an infected computer and prevents the user from unlocking it until a ransom fee has been paid. In some cases, ransomware can lock down an entire hard drive, making it impossible to recover any data.
Until the system has been unlocked, a message is displayed that demands payment for the decryption key. Attackers typically want this payment in the form of bitcoins, which prevent the money from being traced. The vast majority of ransomware attacks are designed for Windows, which has a significantly greater market share than macOS. However, as Apple computers become more popular, the number of attacks targeting Mac users is growing at an unprecedented rate.
Back in April, the latest Threats Report from McAfee Labs revealed that the number of malware attacks built for macOS skyrocketed 744 percent in 2016, with around 460,000 instances of software identified. Fortunately, the vast majority of this is adware, which is nowhere near as harmful.
How is ransomware spread?
Just like a lot of malware infections, ransomware is spread by phishing emails. A seemingly innocent file is attached to a message and an unsuspecting user opens it, believing it to be genuine. The malicious software can then carry out its attack and the user knows nothing about it until it’s too late.
It is believed the WannaCry attack took advantage of an exploit called EternalBlue, developed by the U.S. National Security Agency (NSA), which allows it to be spread through a network.
This means that once the software has been installed on one PC, it can spread itself to others on the same network without having to be opened manually on each computer.
How can you avoid it?
The simplest way to avoid ransomware is to keep your computer up to date. Software vendors typically issue patches for big vulnerabilities — like MS17-010, the one exploited by WannaCry — soon after they are identified, and installing those patches ensures your computer is safe.
Believe it or not, Microsoft patched vulnerability MS17-010 back in March, and categorized the update as “critical.” Despite this, many organizations had failed to apply it, leaving their machines vulnerable. PCs running older operating systems, like Windows XP, were also at risk.
Since WannaCry was identified, Microsoft has taken the unusual step of patching both Windows XP and Windows Server 2003 — despite dropping support over two years ago — to prevent further outbreaks.
You can also bolster your security by running a reputable antivirus program. These can identify certain attacks as soon as they are downloaded and block them before they get a chance to do any damage. But antivirus won’t always save you. Just as quickly as these programs are updated to fight off the latest attacks, hackers are developing new ones that will initially go undetected.
What is being done about WannaCry?
In a nutshell, there’s very little that can be done with computers that are already infected. Experts will be looking at ways in which they can kill it and decrypt systems without paying the ransom fee, but it’s not yet clear if that’s possible.
As mentioned above, Microsoft already addressed the vulnerability exploited by WannaCry back in March, so up-to-date PCs will be immune to it. It has also issued updates for Windows XP and Windows Server 2003 to prevent further attacks.
A 22-year-old security researcher from England inadvertently found a kill-switch in WannaCry that prevents it from spreading. All he had to do was register a “very long nonsensical domain name that the malware makes a request to,” which closed it down.
The kill-switch was baked in by the randsomware’s creator in case they wanted to prevent it from spreading. The software checks the domain and if it identifies it as active, it immediately stops trying to make its way to other machines.
The domain cost the researcher, identified only as MalwareTech, just $10.69, and it was immediately registering thousands of connections every second, according to The Guardian.
But this kill-switch doesn’t spell the end of WannaCry.
“This is not over,” warns MalwareTech. “The attackers will realise how we stopped it, they’ll change the code and then they’ll start again.”
Who has been affected by WannaCry?
The long list of businesses and organizations affected by WannaCry, according to Wikipedia, includes:
- PetroChina
- Public Security Bureau
- Renault
- Portugal Telecom
- Ministry of Foreign Affairs
- MegaFon
- Ministry of Internal Affairs of the Russian Federation
- Russian Railways
- Telefónica
- National Health Service
- NHS Scotland
- Nissan U.K.
- FedEx
- Massachusetts Institute of Technology
- Saudi Telecom Company
- Hitachi
In the U.K., it is believed 70,000 pieces of equipment owned by the NHS have been impacted by the attack, including computers, MRI scanners, blood-storage refrigerators, and theater equipment. Some services and non-critical operations have had to be postponed as a result.
A Nissan factory in Tyne and Wear was forced to halt production after the attack infected some of its systems, while Renault also ceased manufacturing at several sites to prevent the spread of infection.
A wake-up call
In a blog post published by Microsoft on Sunday, the company describes this attack as a “wake-up call.” The company criticizes the NSA for being the source of the vulnerability, and for hoarding vulnerabilities for its own gain. It also insists governments should be doing more to prevent similar attacks.
Microsoft calls on governments to consider the “damage to civilians that comes from hoarding these vulnerabilities.” It wants them to adopt the Digital Geneva Convention with “a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them.”
“We should take from this recent attack a renewed determination for more urgent collective action,” the company concludes. “We need the tech sector, customers, and governments to work together to protect against cybersecurity attacks. More action is needed, and it’s needed now.”