When your Mac’s iSight camera is running, a tiny green light lets you know that it’s turned on. Or at least it’s supposed to. New research from Johns Hopkins University shows how hackers can remotely control the iSight camera in certain Macs without turning on the accompanying LED indicator light.
Apple designed the iSight camera and green light to turn on and off simultaneously as not only a helpful indicator for the user, but a privacy feature. A young man recently pleaded guilty in court to extortion after he performed a remote hack on Miss Teen USA’s webcam to secretly collect nude photos. She had no idea she was hacked as it was happening because her green light never came on.
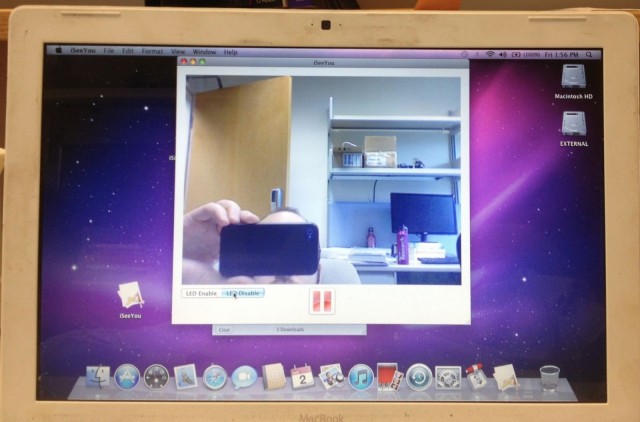
“We describe how to disable the LED on a class of Apple internal iSight webcams used in some versions of MacBook laptops and iMac desktops,” reads the study’s description. “This enables video to be captured without any visual indication to the user and can be accomplished entirely in user space by an unprivileged (non- root) application.”
Two students from Johns Hopkins created a proof-of-concept app called “iSeeYou” to show how the process works. You can read the full report, which includes steps to replicate the hack, by viewing this linked PDF.
To commandeer iSight, the two researchers were able to reprogram the camera’s micro-controller, a dedicated chip that basically acts as the hardware’s own CPU. From there, the camera was told to turn on separately from the light.
The software used to remotely control iSight was Remote Administration Tool (RAT), which is used by IT departments and educational institutions to administer large numbers of computers. The Wikipedia page for RAT details all of the ways it can also be used nefariously through malware.
The documented hack affects “Apple internal iSight webcams found in earlier-generation Apple products, including the iMac G5 and early Intel-based iMacs, MacBooks, and MacBook Pros until roughly 2008.” Renowned security researcher Charlie Miller told The Washington Post that the hack could work on newer Macs as well, but it would require a “lot of work and resources.”
Source: Johns Hopkins University
Via: The Washington Post


