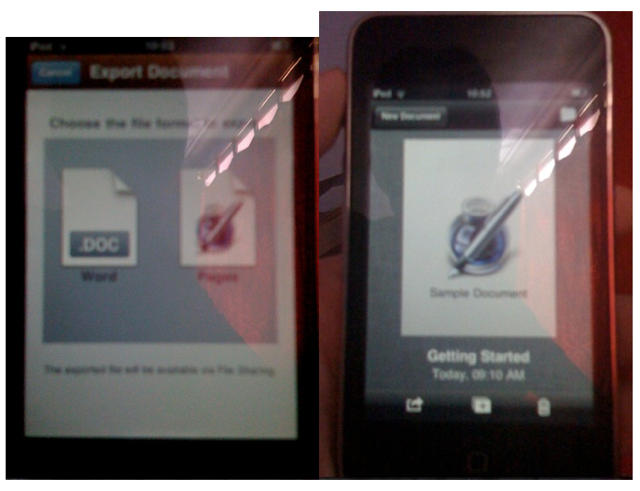
Apple’s accidentally hinted at the existence of iWorks for iPhone a few times in the past now, but these blurry images over at 9to5Mac are the first plausible look at the software, demonstrating a beta of Pages for iPhone running on an iPod Touch.
Sure, this kind of image is something that could be easily spoofed by a programmer with a jailbroken iPhone, but I suspect that it’s legit: with iMovie for iPhone, Apple has already demonstrated itself to be ready to start porting over their desktop apps to iOS.