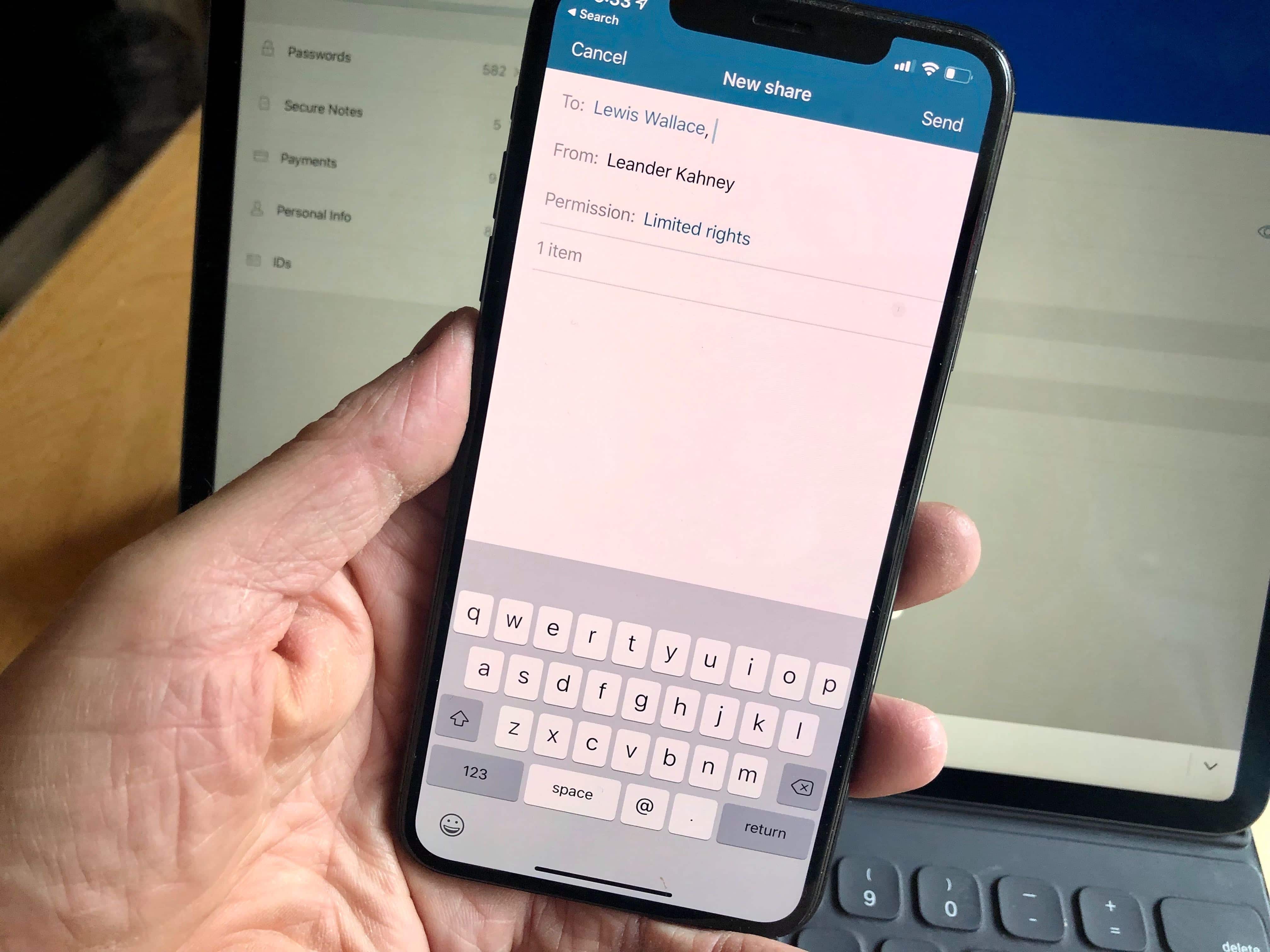
These days, with data breaches on the rise, even companies whose job is to keep you secure online are suffering data disasters. But not security-first password manager Dashlane. It has never been breached. Not every password management company can say that.
Why you can trust Dashlane password management: Never breached, always secure

Photo: Dashlane

![Keep your Apple device’s data secure with this VPN [Deals] This powerful, intuitive VPN is available at a massive discount, so there's no reason not to stay secure online.](https://www.cultofmac.com/wp-content/uploads/2019/04/SaferVPN-1.jpg)


![Become your own cyber security expert with this bundle of lessons [Deals] These 11 lessons will make sure your business is caught up with the complex world of cyber threats and security.](https://www.cultofmac.com/wp-content/uploads/2015/10/26a058711b6c844fb7a797a5bac8ee78690a7649_main_hero_image.jpg)
![How To Set Up FileVault Protection On Your Mac [OS X Tips] Screen Shot 2014-01-14 at 7.08.29 PM](https://www.cultofmac.com/wp-content/uploads/2014/01/Screen-Shot-2014-01-14-at-7.08.29-PM.jpg)

