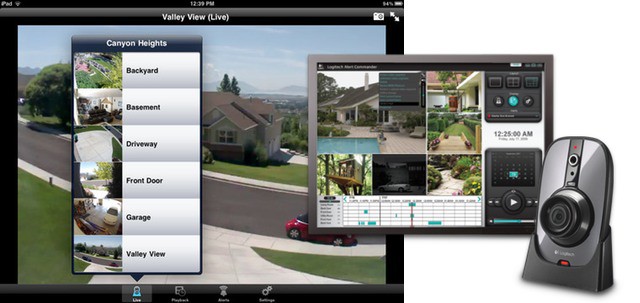
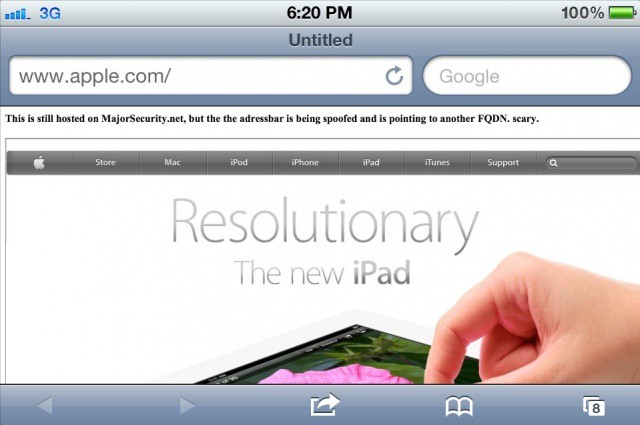
The news that IBM bans Siri for every employee that has an iPhone 4S and participates the company’s BYOD program unleashed a lot of discussion about whether the company was being paranoid or prudent. One of the bigger questions to come out of all that discussion was a reframing of the issue itself – does Siri have a place in the business world to begin with?
Setting aside the security and privacy issues that led IBM to ban Siri, are there compelling use cases for Siri in the workplace? If there are, do they outweigh the privacy and security concerns? Could Apple do more to make Siri business-friendly?
![Does Siri Belong In Business? [Feature] Siri](https://www.cultofmac.com/wp-content/uploads/2012/06/Siri.jpg)



![Was IBM Right? Is Siri A Threat To Businesses? [Feature] IBM bans Siri use on the iPhones of its employees](https://www.cultofmac.com/wp-content/uploads/2012/05/siri-banned.jpg)
![Get Your Gmail Backed Up Where You Need It [Review] A few rough edges, but it works](https://www.cultofmac.com/wp-content/uploads/2012/05/backupg.jpg)


![Slide To Unlock — Your Mac [OS X Tips] Slide to Unlock Mac](https://www.cultofmac.com/wp-content/uploads/2012/05/Slide-to-Unlock-Mac.jpg)


![Face Recognition Photo App Hopes To Sidestep Basic Flaw With A Blink [Review] Dare you show your face?](https://www.cultofmac.com/wp-content/uploads/2012/04/facevault1.jpg)