For the first time, an iOS trojan has been spotted in the wild. Adapted from a well-known Android trojan, GoldDigger, the new malware is called GoldPickaxe, according to a new report. And it steals an iPhone user’s facial recognition data to go after money in banking and other financial apps. We’ll show you how below.
First iOS trojan, GoldPickaxe, steals facial recognition data to access bank accounts
Malware, including trojans designed to look like innocent programs, has appeared on Macs. But this looks like the first one designed to invade the iPhone (and steal your money).
An offshoot of the GoldDigger banking malware first discovered in October 2023, GoldPickaxe has different versions that try to drain bank accounts via Android and iOS devices, according to a new report from cybersecurity company Group-IB.
So far the GoldPickaxe.iOS trojan is active in Southeast Asia but that could easily expand to other countries, the group said.
How does GoldPickaxe.iOS work?
Once downloaded to a device, the malware collects facial-recognition data, identifies documents and reads text messages for the “threat actor” behind the scheme, codenamed “GoldFactory.”
The download usually comes in the form of a fake government app mistook for genuine. Once active on a device, the trojan manipulates functions in the background. It can capture the victim’s face, read SMS messages, request ID documents and proxy network traffic, for example.
That doesn’t sound good. And GoldPickaxe’s use of stolen biometric data sounds even worse because it can enables bank-account access, according to Group-IB:
To exploit the stolen biometric data, the threat actor utilizes AI-driven face-swapping services to create deepfakes. This data combined with ID documents and the ability to intercept SMS, enables cybercriminals to gain unauthorized access to the victim’s banking account – a new technique of monetary theft, previously unseen by Group-IB researchers in other fraud schemes.
Notably, Group-IB said the malware exhibits less malicious functionality on iOS devices than Android devices because of Apple’s stronger security. On Android, for example, it can perform clicks on the screen, download 100 recent photos, serve fake notifications and more.
And while the malware can capture a victim’s likeness, it does not capture encrypted Face ID data.
How is it distributed?
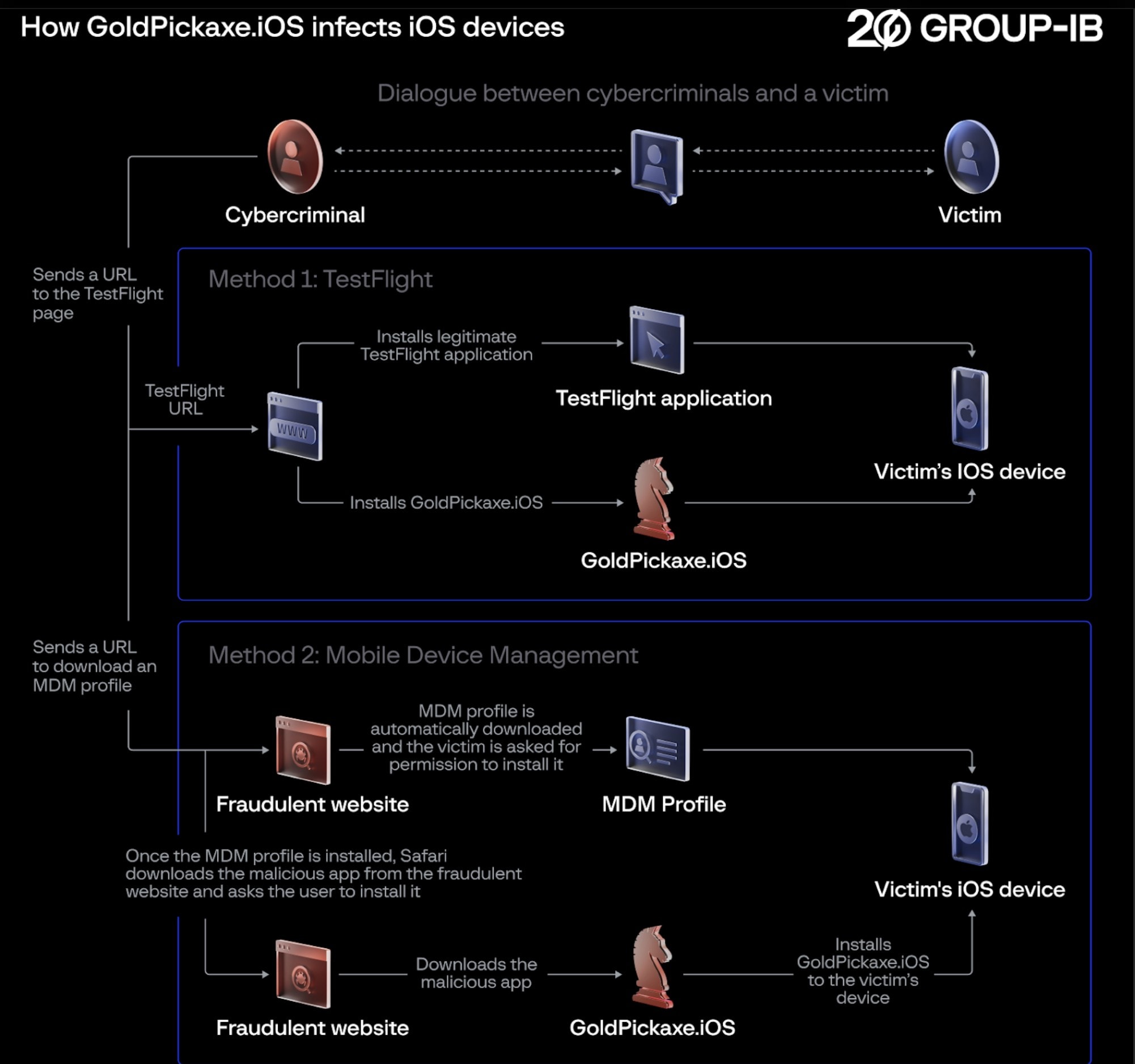
Photo: Group-IB
The researchers also found the distribution scheme for GoldPickaxe “notable. ” That’s because its stalled effort to exploit Apple’s TestFlight mobile-app testing platform resulted in an even more devious scheme involving phishing:
The threat actor utilized Apple’s mobile application testing platform, TestFlight, to distribute malware initially. Following the removal of its malicious app from TestFlight, the threat actor adopted a more sophisticated approach. They employed a multi-stage social engineering scheme to persuade victims to install a Mobile Device Management (MDM) profile. This allowed the threat actor to gain complete control over the victim’s device.
Victims of the new malware so far have been located in Thailand and Vietnam. Group-IB said it’s likely to expand operations beyond those countries, however.
We first published this article on February 19, 2024, and then updated it with more details on February 22, 2024.
![First-ever iOS trojan steals your face to break your bank [Updated] Trojan horse: first ios trojan goldpickaxe](https://www.cultofmac.com/wp-content/uploads/2024/02/pexels-kemal-hayit-6474435-1536x1022.jpg)

