iOS hacker and security researcher Pod2g has uncovered a major SMS security flaw with the iPhone that could lead to text message spoofing. The problem is with the way in which the iPhone handles text messages, and it’s present in the latest version of iOS — including the iOS 6 beta 4 release. However, Pod2g insists he’s pleading with Apple to get it fixed.
In a post on his blog, Pod2g explains the issue, and why it’s a particular problem with the iPhone:
A SMS text is basically a few bytes of data exchanged between two mobile phones, with the carrier transporting the information. When the user writes a message, it is converted to PDU (Protocol Description Unit) by the mobile and passed to the baseband for delivery.
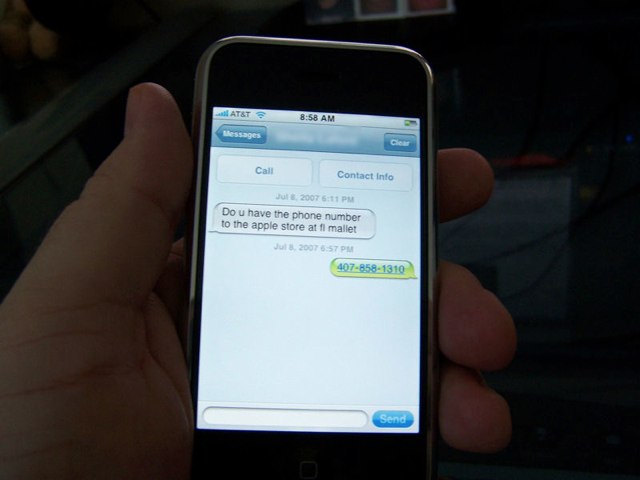
[…] In the text payload, a section called UDH (User Data Header) is optional but defines lot of advanced features not all mobiles are compatible with. One of these options enables the user to change the reply address of the text. If the destination mobile is compatible with it, and if the receiver tries to answer to the text, he will not respond to the original number, but to the specified one.
Most carriers don’t check this part of the message, which means one can write whatever he wants in this section : a special number like 911, or the number of somebody else.
Why is this a problem with the iPhone? Because on the iPhone, when you receive a text message, you only see the “reply-to” number — not the original one. Pod2g then provides a number of examples in which this could be a serious security issue.
For example, it could be used to send phishing that appear to come from your bank, but actually go to a different recipient when you reply.
It’s unclear how easy it is for hackers to intercept your messages, but Pod2g considers this a “severe” security flaw. He also explained that he’s confident other security researchers will already be aware of the issue, and “some pirates as well.”
Source: Pod2g
Via: iDownloadBlog