It hasn’t been a good year for Mac security so far, at least PR-wise, and it’s about to get a lot uglier: an Apple programmer forgot to turn off a debug switch in OS X 10.7.3’s security settings before the update was distributed to the public.
The result? If you’re running OS X 10.7.3, your login password might be stored in plain text on an unencrypted, easily accessed section of your hard drive.
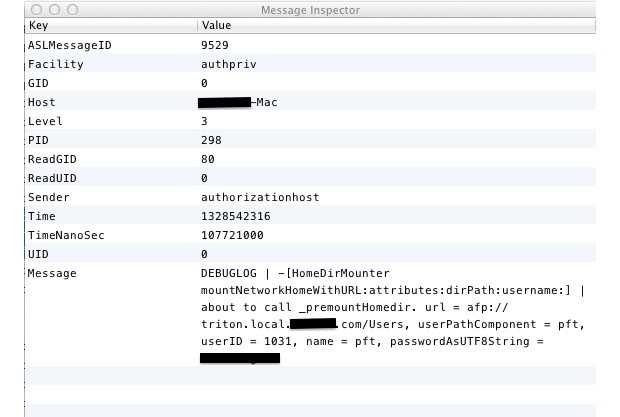
The massive SNAFU was discovered by security researcher David Emery, who claims that all user login passwords are being stored in a system-wide debug log file in real text in some distributions of the latest Apple security update to Lion, OS X 10.7.3.
According to Emery, this is a serious issue, as this file and all the passwords contained within can be easily accessed by anyone with physical or remote access to your computer:
This is worse than it seems, since the log in question can also be read by booting the machine into firewire disk mode and reading it by opening the drive as a disk or by booting the new-with-LION recovery partition and using the available superuser shell to mount the main file system partition and read the file. This would allow someone to break into encrypted partitions on machines they did not have any idea of any login passwords for.
Worse, it affects Time Machine backups on external drives, and even computers using Filevailt aren’t safe from having hackers access the log file.
According to Emery, the best way to protect yourself until Apple patches this whole is to use Filevault 2’s whole disk encryption, as well as requiring a firmware password to prevent would be hackers from gaining access to the disk by booting the computer in FireWire Disk Mode.
It seems unlikely that Apple won’t rush a fix to this issue out in the coming days, but in the aftermath of Flashback, a stupid screw-up like this is ill-timed. Consumers are already starting to worry that Macs might not be as secure as they have traditionally thought. Apple doesn’t need to help that argument out by forgetting to re-secure user’s systems before they send out the latest OS X update.