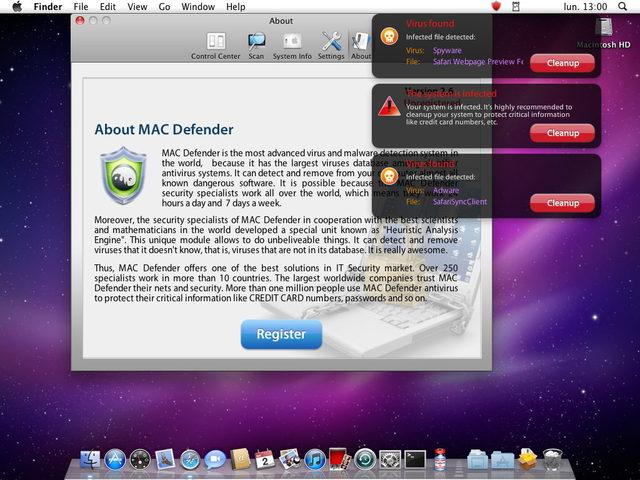
Apple may be preparing to nuke Mac Defender from orbit in the next Snow Leopard update, but not only is the malware still a very real threat… Mac Defender now mutated into an even bigger danger than it was before.
Mac antivirus company Intego just wrote to us to alert us to the latest variant of Mac Defender, called Mac Guard. What makes Mac Guard so dangerous compared to previous variants (including MacDefender, MacProtector and MacSecurity) is that Mac Guard doesn’t need you to enter your administrator’s password in order to install itself.
Here’s how it works:
The first part is a downloader, a tool that, after installation, downloads a payload from a web server. As with the Mac Defender malware variants, this installation package, called avSetup.pkg, is downloaded automatically when a user visits a specially crafted web site.
If Safari’s “Open ‘safe’ files after downloading” option is checked, the package will open Apple’s Installer, and the user will see a standard installation screen. If not, users may see the downloaded ZIP archive and double-click it out of curiosity, not remembering what they downloaded, then double-click the installation package. In either case, the Mac OS X Installer will launch.
Unlike the previous variants of this fake antivirus, no administrator’s password is required to install this program. Since any user can install software in the Applications folder, a password is not needed. This package installs an application – the downloader – named avRunner, which then launches automatically. At the same time, the installation package deletes itself from the user’s Mac, so no traces of the original installer are left behind.
The second part of the malware is a new version of the MacDefender application called MacGuard. This is downloaded by the avRunner application from an IP address that is hidden in an image file in the avRunner application’s Resources folder. (The IP address is hidden using a simple form of steganography.)
As with other variants of Mac Defender, Mac Guard is easy enough to avoid if you know what you’re looking for, and remove if you accidentally become infected.
However, now that Mac Defender has made the leap to infecting users’ machines without entering an administrator’s password first, it’s likely a lot more people are going to be infected. Apple’s security update can’t come soon enough.