BYOD programs have a tendency to worry IT departments. After decades of being charged with keeping computers, supporting devices, and data safe and in working order, losing control of hardware is a massive culture shift. Even absent a BYOD program, the growing number of mobile devices that are used outside of the office and take corporate data outside the security of an enterprise network can be disorienting for long term IT professionals.
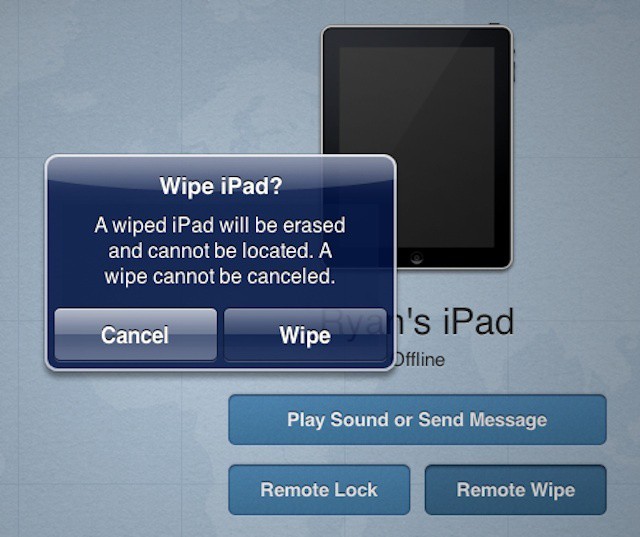
That leads to a tendency to clamp down with every ounce of security muscle available – mobile device management (MDM) can’t entirely secure an iPhone or iPad, but they can do a pretty good job of locking it down, monitoring it in the office or on the road, and make it easy to wipe everything off of it at a moment’s notice.
As InfoWorld’s Galen Gruman noted this morning, years of IT experience devoted to keeping data safe has led to an instinct to wipe data from mobile devices, including employee personal devices, as soon as it’s reported missing. While understandable, this approach is apt to create more problems than it solves.
The tension that exists between users and IT is becoming palpable in many businesses these day. Employees have discovered the potential of non-IT solutions. iPhone, iPad, iCloud, DropBox, Google Docs, Google Voice, and an endless litany of so-called consumer technologies work better than many locked down, secured, and limited solutions that IT delivers.
That tension can lead to distrust between IT staff and the rest of the employees in an organization. It can lead to employees rejecting a BYOD program while still bringing their iPhone to meetings and presentations, using it to take notes, review data, and even create business documents – all cut off from any protective measures implemented by IT.
With that tension in the air, IT can’t afford to be overly controlling – especially with someone’s iPhone or iPad that they bought with their own money. Backing away from the urge to wipe a device immediately can gain two forms of political or social capital.
First, users are less likely to see IT as the enemy. Second, they’re more likely to report a lost device immediately rather than waiting to see if they can find it. As Galen points out, most mobile management solutions give IT departments wider options than wiping personal emails, family photos, and other kinds of personal data along with business content.
Adopting a remote lock and then wipe policy that gives users two or three hours to recover a missing device and/or a policy to revoke and wipe just business information can be worth the investment in mobile management solutions that offer these options. It will ultimately help build goodwill and because users are more likely to admit a device is missing, it can ultimately boost security. Perhaps even more important, with the range of solutions on the market, there’s a good chance of finding one that delivers other security advantages and valuable features.
Source: InfoWorld