For many IT shops, the iPad and/or the iPhone can be a conundrum. While iOS has built-in enterprise capabilities, they may not be immediately apparent. There’s also the fact that Apple doesn’t act the same way as most enterprise vendors. Apple does offer enterprise sales and support teams, training and certification programs, and a solid selection of enterprise-related resources, but rarely promotes them. This can be disorienting and frustrating to most IT professionals.
Often there’s a sense of urgency around getting iOS devices integrated securely that adds to this stress – it can be because executives want them, users are bringing them in and doing work on them already with no regard for IT or policies, or because there’s been a decision to offer iPads to specific users or groups.
The ideal beginning when faced with this prospect is to take a deep breath and then to begin breaking down the issues that need to be addressed and prioritizing and handling them. As with other major IT projects, you’ll probably need to develop stop-gap measures to keep things running until your final solution is ready to be rolled out.
The first step is to determine if there are iOS devices in your organization already? If so, who’s are they and how are they being used. Network monitoring tools can give you a good deal of information about how many devices are on your network and, to some extent, where they are in your organization. You may also be able to tell who is using them if you use RADIUS authentication for your wireless network or if users have setup access to their Exchange mailbox (or other email/messaging systems) on their device since these would require a user account. Getting a truly clear picture, however, is going to take some legwork and reaching out to the people using iPads or iPhones in order to understand how and why they’re using them.
If they aren’t already iOS devices out there, then you need to determine who is going to be using iPads and iPhones – those that your company purchases and/or through a BYOD program. You also need to determine how different groups of users can be expected to use them.
The next piece of the puzzle is to determine how you can get some form of mobile management and iOS support in place quickly. This is particularly important if you already have a lot of unmanaged devices on your network, but even if you don’t and you have the luxury of planning a roll out of devices or a BYOD program, you may still want to get things up and running quickly.
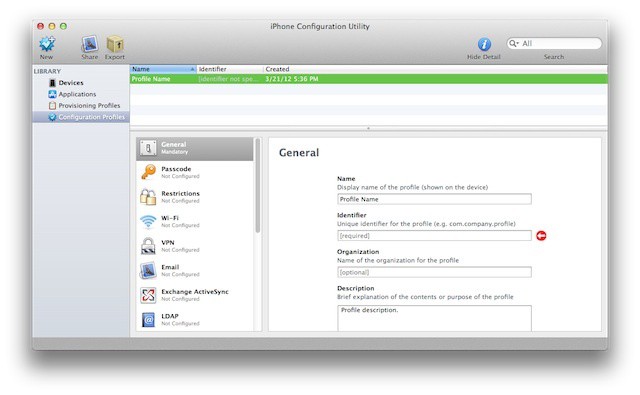
There are a couple of different options here. You can round up the devices already out there and apply management to them. This may not be practical in larger organizations but it is an option in small and mid-size businesses. You can use Apple’s iPhone Configuration Utility to set configuration profiles on devices either by physically connecting them to an admin workstation or by emailing the profiles (or a link to a web server hosting them) to users and require them to install them. This latter approach works best if you’re confident that you can monitor that users have installed them. If you go this route and you’re working with employee-owned devices, iPhone Configuration Utility is a better option than Apple’s new Configurator tool, which will wipe a device before applying profiles.
One silver lining here is that all mobile device management vendors implement that same set of iOS configuration options. They differentiate in other ways (features, cost, additional platforms, etc.) but Apple pretty much created a single set of MDM capabilities and they’re based on what you can do with configuration profiles in either iPhone Configuration Utility or Apple Configurator (the difference is that MDM vendors also have access to a set of Apple-provided device monitoring capabilities). That means that the choices you make at this stage should shift over to a more powerful management tool fairly easily later on.
Another option is to modify your network to account for these devices while reducing the exposure they have to your overall network and resources. A common approach is to create a separate Wi-Fi network that has very limited access to key systems and resources but allows basic access to the Internet and some systems like email – this is easiest in business where a guest or limited access network already exists. Hardening key systems and restricting access based on the type of device or mobile browser is another possibility.
Regardless which of these avenues you decide on (and deciding on both is an option as well), you’ll need to contact the current iOS users in your organization and inform that you’re implementing policies around iPads and iPhones throughout your organization. This means that you need to determine exactly what policies your organization will need to enforce. Although it’s possible to come up with some basic policies to deal with the immediate situation and revisit them later, it’s a far better option to think about your ultimate needs now. That way, you’ll be setting expectations from the get-go even if you may not immediately enforce those policies.
This process requires buy-in from senior management, particularly if you expect to take corrective action when policies are violated (reducing a user’s access to resources or speaking with either his or her manager or HR about the violations). Since getting these policies approved will probably take some political capital, it’s best to take care of the eventual policies the first time rather than repeatedly asking for executive support of new or different policies.
At this point, you should have a reasonably functional stop-gap solution. Now it’s time to take another deep breath and begin to determine what your ultimate solution will be. This is a good time to read up on what other organizations have done and ask questions of IT professionals who have been through this process. That will give you a lot of background in terms of whether you want to take a managed device approach, a managed data and information approach, or a combination of the two.
Unless you’re a small organization with just a handful of users, you’ll probably need a more robust set of tools than the iPhone Configuration Utility or Apple Configurator. That means, that once everything is set with your stop-gap option, you’ll need to start determining what mobile management product(s) you want to deploy as a final solution. There are dozens of options for device, app, and information management and they each have their own advantages and disadvantages. As with the selection of any other vendor, you’ll want to narrow your choices and then test each of those and do a pilot project on the best candidate(s) before moving forward with a large scale rollout.